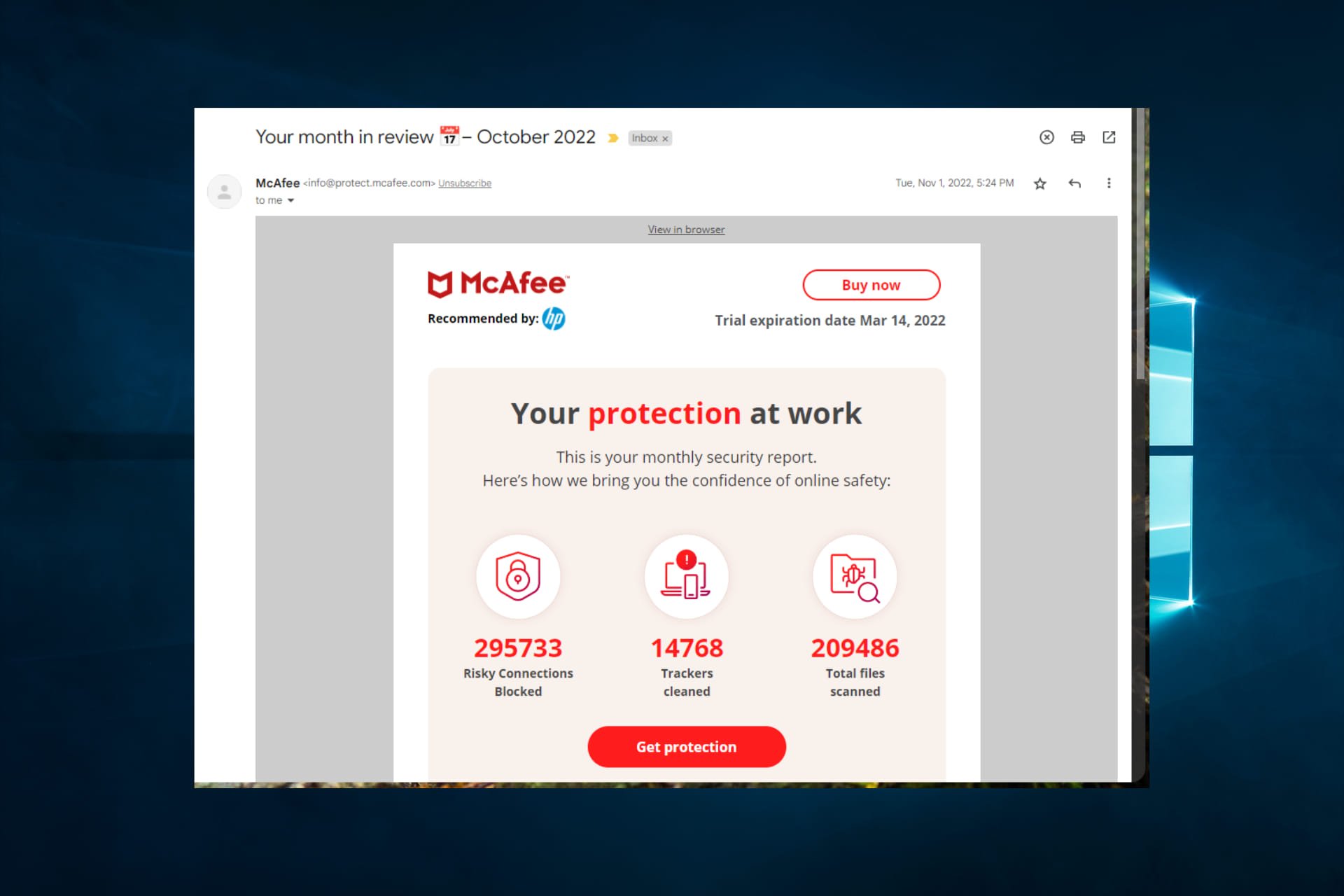
Receiving an email with the subject line "McAfee Your Info Was Stolen" can be alarming, but it's crucial to approach it with caution and verify its authenticity. In today's digital age, cybercriminals are constantly devising new ways to exploit vulnerabilities and steal sensitive information. One such method involves sending phishing emails that appear to be from trusted cybersecurity companies like McAfee. These emails often claim that your personal information has been compromised and urge you to take immediate action. However, before you panic or click on any links, it's essential to understand what these emails are, how to identify them, and what steps you should take to protect yourself.
Phishing emails are a common tactic used by cybercriminals to trick individuals into divulging personal information, such as passwords, credit card numbers, or Social Security numbers. These emails often mimic legitimate communications from reputable companies, making it difficult for recipients to distinguish between real and fake messages. The "McAfee Your Info Was Stolen" email is one such example, and falling victim to it could have serious consequences for your online security. This article will guide you through everything you need to know about this type of email, including how to spot it, what to do if you receive it, and how to safeguard your data against future threats.
In the following sections, we will delve deeper into the anatomy of phishing emails, explore real-life examples of similar scams, and provide actionable steps to ensure your information remains secure. By the end of this article, you will have a comprehensive understanding of how to handle suspicious emails and protect yourself from potential cyberattacks. Let's begin by examining what phishing emails are and why they are so dangerous.
Read also:Harris Faulkner Illness Understanding The Challenges And Triumphs
- What Are Phishing Emails?
- Anatomy of the "McAfee Your Info Was Stolen" Email
- How to Identify a Phishing Email
- Steps to Take If You Receive the Email
- Protecting Your Personal Information
- Common Scams and How to Avoid Them
- Real-Life Examples of Phishing Attacks
- McAfee Support and Resources
- Best Practices for Online Security
- Conclusion
What Are Phishing Emails?
Phishing emails are fraudulent messages designed to deceive recipients into revealing sensitive information or performing actions that compromise their security. These emails often appear to come from trusted sources, such as banks, government agencies, or well-known companies like McAfee. Cybercriminals use sophisticated techniques to make these emails look legitimate, including replicating official logos, mimicking email addresses, and crafting urgent or alarming subject lines.
The primary goal of phishing emails is to trick recipients into clicking malicious links, downloading harmful attachments, or providing personal information. Once the attacker gains access to this data, they can use it for identity theft, financial fraud, or other malicious activities. According to a report by the Anti-Phishing Working Group (APWG), phishing attacks have increased by over 60% in recent years, making them one of the most prevalent cyber threats today.
How Phishing Works
Phishing attacks typically follow a predictable pattern:
- Baiting: The attacker sends an email that appears legitimate, often using fear or urgency to prompt action.
- Hooking: The recipient clicks on a link or provides information, unknowingly giving the attacker access to their data.
- Exploiting: The attacker uses the stolen information for malicious purposes, such as draining bank accounts or selling it on the dark web.
Anatomy of the "McAfee Your Info Was Stolen" Email
The "McAfee Your Info Was Stolen" email is a classic example of a phishing attempt. It often begins with a subject line designed to grab attention, such as "Urgent: Your Personal Data Has Been Compromised." The body of the email typically includes alarming statements, such as claims that your account has been hacked or that your personal information is being sold on the dark web. To add credibility, the email may include McAfee's logo and mimic the company's official communication style.
One common feature of these emails is a call-to-action button or link that urges recipients to "Secure Your Account" or "Verify Your Information." Clicking on these links often leads to fake websites designed to steal login credentials or other sensitive data. In some cases, the email may also include attachments that, when opened, install malware on the recipient's device.
Red Flags to Watch For
Here are some warning signs that can help you identify a phishing email:
Read also:Remoteiot Platform Ssh Key Free Android A Comprehensive Guide
- Generic greetings, such as "Dear Customer" instead of your name.
- Poor grammar and spelling mistakes.
- Urgent or threatening language designed to provoke immediate action.
- Suspicious email addresses that do not match McAfee's official domain.
- Links that lead to unfamiliar or misspelled URLs.
How to Identify a Phishing Email
Identifying a phishing email requires a keen eye and a healthy dose of skepticism. Here are some tips to help you spot these fraudulent messages:
1. **Check the Sender's Email Address:** Always verify the sender's email address. Phishing emails often use addresses that mimic official ones but contain slight variations or misspellings. For example, "support@mcafee.com" might be altered to "support@mcafeesecurity.com."
2. **Examine the Content:** Look for inconsistencies in the email's content. Phishing emails often include vague or generic language, such as "Dear Valued Customer," instead of addressing you by name. They may also contain urgent requests or threats to prompt immediate action.
3. **Hover Over Links:** Before clicking on any links, hover your mouse over them to preview the URL. If the link directs to an unfamiliar or suspicious website, do not click on it.
Additional Tips
- Avoid downloading attachments from unknown or unverified sources.
- Contact the company directly using official contact information to verify the email's authenticity.
- Use email filtering tools to block suspicious messages.
Steps to Take If You Receive the Email
If you receive an email claiming that your information was stolen, it's essential to act quickly and cautiously. Here are the steps you should follow:
1. **Do Not Click Any Links or Download Attachments:** The first rule of handling suspicious emails is to avoid interacting with them. Clicking on links or downloading attachments can expose your device to malware or phishing attempts.
2. **Verify the Email's Authenticity:** Contact McAfee's official customer support team using the contact information listed on their official website. Do not use any contact details provided in the email itself.
3. **Report the Email:** Forward the suspicious email to your email provider's spam or phishing reporting service. Many providers, such as Gmail and Outlook, have dedicated addresses for reporting phishing attempts.
Additional Actions
- Change your passwords for any accounts that may have been compromised.
- Enable multi-factor authentication (MFA) for added security.
- Monitor your financial accounts for any unauthorized transactions.
Protecting Your Personal Information
Preventing phishing attacks requires a proactive approach to online security. Here are some strategies to help safeguard your personal information:
1. **Use Strong, Unique Passwords:** Avoid using the same password across multiple accounts. Instead, create strong, unique passwords for each of your accounts and consider using a password manager to keep track of them.
2. **Enable Multi-Factor Authentication (MFA):** MFA adds an extra layer of security by requiring a second form of verification, such as a text message code or fingerprint scan, in addition to your password.
3. **Keep Software Updated:** Regularly update your operating system, antivirus software, and other applications to protect against known vulnerabilities.
Additional Security Measures
- Use a virtual private network (VPN) to encrypt your internet connection.
- Be cautious when sharing personal information online.
- Educate yourself and your family about common phishing tactics.
Common Scams and How to Avoid Them
Phishing emails are just one type of scam that cybercriminals use to exploit unsuspecting individuals. Other common scams include:
1. **Tech Support Scams:** These scams involve fraudsters posing as technical support representatives from companies like McAfee. They often claim that your computer is infected with malware and request remote access to "fix" the issue.
2. **Fake Prize or Lottery Scams:** These emails inform recipients that they have won a prize or lottery and require them to provide personal information or pay a fee to claim their winnings.
3. **Romance Scams:** Cybercriminals create fake profiles on dating websites or social media platforms to build relationships with victims and eventually request money or personal information.
How to Avoid Scams
- Never share personal or financial information with unknown individuals or organizations.
- Be skeptical of unsolicited offers or requests for money.
- Verify the legitimacy of any company or individual before providing information or making payments.
Real-Life Examples of Phishing Attacks
Phishing attacks have affected millions of individuals and organizations worldwide. Here are some notable examples:
1. **The 2016 Democratic National Committee (DNC) Hack:** Cybercriminals used phishing emails to gain access to the DNC's email servers, leading to the leak of sensitive information during the U.S. presidential election.
2. **The 2013 Target Data Breach:** Attackers used phishing emails to steal login credentials from a third-party vendor, allowing them to access Target's payment systems and compromise the data of over 40 million customers.
3. **The 2020 Twitter Bitcoin Scam:** Cybercriminals gained access to high-profile Twitter accounts, including those of Elon Musk and Barack Obama, by using a phishing attack to trick employees into revealing their credentials.
Lessons Learned
- Phishing attacks can have far-reaching consequences, affecting individuals, businesses, and even governments.
- Employee training and awareness are critical to preventing phishing attacks.
- Implementing robust security measures can help mitigate the impact of these attacks.
McAfee Support and Resources
If you suspect that you have fallen victim to a phishing attack or need assistance with online security, McAfee offers a range of support and resources to help you. Here are some key resources to explore:
1. **McAfee's Official Website:** Visit McAfee's website to access articles, guides, and FAQs about online security and phishing prevention.
2. **Customer Support:** McAfee provides 24/7 customer support via phone, email, and live chat. Be sure to use the official contact information listed on their website.
3. **Security Tools:** McAfee offers a variety of security tools, including antivirus software, identity theft protection, and secure browsing solutions.
Additional Resources
- Download McAfee's mobile app for on-the-go security.
- Sign up for McAfee's newsletter to stay informed about the latest threats and security tips.
- Participate in McAfee's online community forums to connect with other users and share experiences.
Best Practices for Online Security
Maintaining online security requires a combination of vigilance, education, and the right tools. Here are some best practices to follow