Setting up SSH for an IoT router is essential for ensuring secure communication and remote access to your network. With the increasing number of IoT devices connected to networks, securing these devices has become more critical than ever. SSH, or Secure Shell, provides a secure way to access your router remotely, encrypting data and protecting it from unauthorized access. In this article, we’ll explore everything you need to know about SSH IoT router setup, including step-by-step instructions, best practices, and security tips.
IoT routers are the backbone of smart home and industrial IoT systems, managing communication between devices and the internet. Without proper security measures, these routers can become vulnerable to cyberattacks. SSH is a powerful tool that not only enhances security but also simplifies remote management. Whether you’re a network administrator or a tech-savvy homeowner, understanding how to configure SSH on your IoT router is crucial for maintaining a secure and efficient network.
In the following sections, we’ll delve deeper into the technical aspects of SSH, its role in IoT security, and a detailed guide to setting it up on your router. By the end of this article, you’ll have the knowledge and tools to implement SSH effectively, ensuring your IoT devices are protected from potential threats.
Read also:Wilma Flintstone The Iconic Matriarch Of Bedrockrsquos First Family
Table of Contents
- What is SSH and Why is it Important for IoT Routers?
- Benefits of Using SSH for IoT Router Setup
- Prerequisites for Setting Up SSH on IoT Routers
- Step-by-Step Guide to SSH IoT Router Setup
- Troubleshooting Common SSH Setup Issues
- Security Best Practices for SSH IoT Router Setup
- Advanced SSH Configuration for IoT Routers
- Tools and Resources for Managing SSH on IoT Routers
- Real-World Applications of SSH in IoT Networks
- Conclusion and Call to Action
What is SSH and Why is it Important for IoT Routers?
SSH, or Secure Shell, is a cryptographic network protocol used for secure communication over an unsecured network. It provides a secure channel for remote access, file transfers, and command execution. In the context of IoT routers, SSH plays a vital role in ensuring secure remote management and protecting sensitive data from cyber threats.
IoT routers are often targeted by hackers due to their role as gateways to connected devices. Without proper security measures, these routers can expose your entire network to risks such as data breaches, unauthorized access, and malware attacks. SSH addresses these concerns by encrypting all communication between the router and remote devices, making it nearly impossible for attackers to intercept or manipulate data.
Key Features of SSH
- Encryption: SSH uses strong encryption algorithms to protect data in transit.
- Authentication: It supports multiple authentication methods, including passwords and key-based authentication.
- Portability: SSH is compatible with various operating systems and devices, making it versatile for IoT environments.
Benefits of Using SSH for IoT Router Setup
Implementing SSH on your IoT router offers numerous advantages, particularly in terms of security and efficiency. Below are some of the key benefits:
1. Enhanced Security
SSH encrypts all communication between the router and remote devices, preventing eavesdropping and man-in-the-middle attacks. This is especially important for IoT routers, which often handle sensitive data such as login credentials and device configurations.
2. Remote Management
With SSH, you can securely access and manage your IoT router from anywhere in the world. This is particularly useful for network administrators who need to troubleshoot issues or update configurations remotely.
3. Compatibility
SSH is widely supported across different platforms and devices, making it a universal solution for securing IoT networks. Whether you’re using a Linux-based router or a proprietary IoT device, SSH can be implemented with minimal effort.
Read also:Tallulah Lloyd Exploring The Life And Career Of A Rising Star
4. Automation and Scripting
SSH allows you to automate tasks such as backups, updates, and monitoring through scripts. This not only saves time but also reduces the risk of human error.
Prerequisites for Setting Up SSH on IoT Routers
Before you begin configuring SSH on your IoT router, there are a few prerequisites you need to address:
1. Firmware Compatibility
Ensure that your router’s firmware supports SSH. Many modern routers come with built-in SSH capabilities, but older models may require a firmware update or third-party software installation.
2. Access to Router Settings
You’ll need administrative access to your router’s settings. This typically involves logging in to the router’s web interface using a username and password.
3. SSH Client
To connect to your router via SSH, you’ll need an SSH client. Popular options include PuTTY for Windows and OpenSSH for Linux and macOS.
4. Public and Private Keys
For enhanced security, consider using key-based authentication instead of passwords. This involves generating a pair of public and private keys and configuring your router to accept the public key.
Step-by-Step Guide to SSH IoT Router Setup
Follow these steps to configure SSH on your IoT router:
Step 1: Enable SSH on the Router
Access your router’s web interface and navigate to the settings menu. Look for an option labeled “SSH” or “Remote Access” and enable it. Some routers may require you to specify a port number for SSH connections.
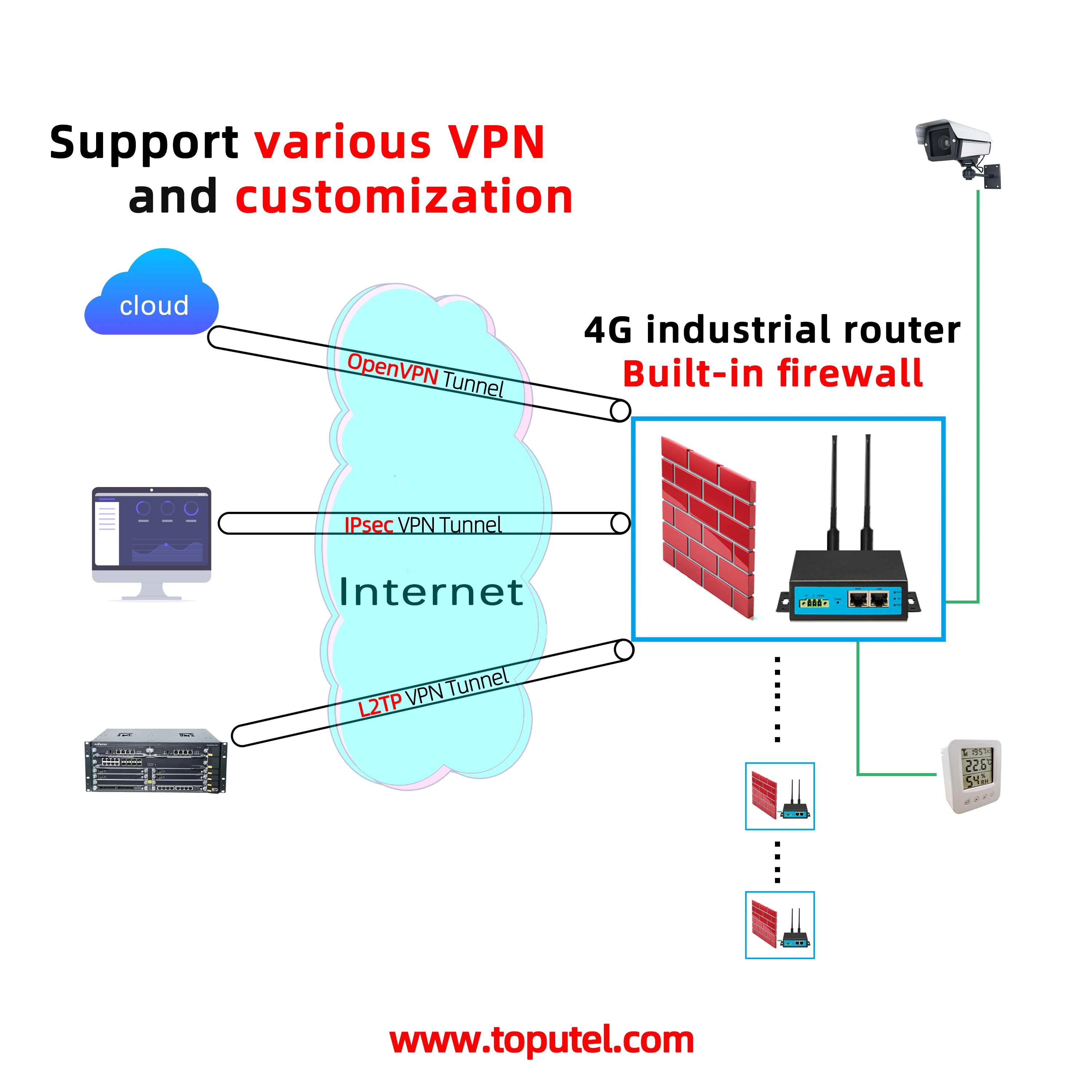
Step 2: Configure Firewall Rules
Ensure that your router’s firewall allows SSH traffic. This typically involves creating a rule to permit incoming connections on the SSH port (default is 22).
Step 3: Set Up Key-Based Authentication
Generate a public-private key pair using an SSH client. Copy the public key to your router’s configuration file and disable password-based authentication for added security.
Step 4: Test the SSH Connection
Use your SSH client to connect to the router. Enter the router’s IP address, port number, and private key. If everything is configured correctly, you should gain access to the router’s command-line interface.
Troubleshooting Common SSH Setup Issues
Despite its benefits, setting up SSH on an IoT router can sometimes be challenging. Below are some common issues and their solutions:
1. Connection Refused
If your SSH client fails to connect, ensure that SSH is enabled on the router and that the correct port is open. Double-check the router’s IP address and firewall settings.
2. Authentication Failure
Authentication issues often arise from incorrect key configurations. Verify that the public key is correctly added to the router’s configuration file and that the private key matches.
3. Slow Performance
Slow SSH connections can result from network congestion or high latency. Use tools like ping and traceroute to diagnose network issues and optimize your router’s performance.
Security Best Practices for SSH IoT Router Setup
Securing your SSH configuration is crucial for protecting your IoT network. Below are some best practices to follow:
1. Use Strong Passwords
If you’re using password-based authentication, ensure that your passwords are strong and unique. Avoid using default credentials provided by the router manufacturer.
2. Change Default Ports
To reduce the risk of brute-force attacks, change the default SSH port (22) to a non-standard port number.
3. Disable Root Login
Prevent unauthorized access by disabling root login and creating a separate user account with limited privileges for SSH access.
4. Regularly Update Firmware
Keep your router’s firmware up to date to patch known vulnerabilities and ensure optimal performance.
Advanced SSH Configuration for IoT Routers
For users seeking more control over their SSH setup, advanced configurations can provide additional security and functionality.
1. Two-Factor Authentication
Implement two-factor authentication (2FA) to add an extra layer of security to your SSH connections. This typically involves using a mobile app to generate one-time codes.
2. Port Knocking
Port knocking is a technique that hides your SSH port until a specific sequence of connection attempts is made. This makes it harder for attackers to detect and exploit your SSH service.
3. Logging and Monitoring
Enable logging for SSH connections to monitor access attempts and detect suspicious activity. Use tools like fail2ban to automatically block IP addresses that exhibit malicious behavior.
Tools and Resources for Managing SSH on IoT Routers
Several tools and resources can simplify SSH management and enhance security:
1. OpenSSH
OpenSSH is a widely used SSH client and server that supports advanced features such as key-based authentication and port forwarding.
2. PuTTY
PuTTY is a lightweight SSH client for Windows users. It offers a user-friendly interface and supports various encryption algorithms.
3. Fail2Ban
Fail2Ban is a tool that monitors SSH logs and automatically bans IP addresses that exhibit malicious behavior, such as repeated failed login attempts.
Real-World Applications of SSH in IoT Networks
SSH is widely used in various industries to secure IoT networks and devices. Below are some real-world applications:
1. Smart Homes
In smart home systems, SSH is used to remotely manage IoT devices such as smart thermostats, cameras, and lighting systems.
2. Industrial IoT
Industrial IoT networks rely on SSH to secure communication between sensors, controllers, and cloud platforms.
3. Healthcare
SSH is used in healthcare IoT systems to protect sensitive patient data and ensure secure communication between medical devices and servers.
Conclusion and Call to Action
Setting up SSH for your IoT router is a critical step in securing your network and protecting your devices from cyber threats. By following the steps outlined in this guide, you can ensure that your router is configured for secure remote access and efficient management.
We hope this article has provided you with valuable insights into SSH IoT router setup. If you found this guide helpful, please consider sharing it with others who might benefit. Additionally, feel free to leave a comment below with any questions or feedback. For more articles on IoT security and networking, explore our blog and stay updated with the latest trends and best practices.