Managing SSH keys in AWS is a critical aspect of securing your cloud infrastructure. With the increasing reliance on cloud services, ensuring robust SSH key management is no longer optional—it’s essential. AWS SSH key management best practices not only protect your data but also streamline access control, reduce vulnerabilities, and enhance operational efficiency. In this article, we’ll delve into the nuances of SSH key management on AWS, offering actionable insights and strategies to safeguard your environment. Whether you’re a seasoned cloud engineer or a newcomer to AWS, understanding these best practices will empower you to fortify your cloud infrastructure effectively.
SSH (Secure Shell) keys are the backbone of secure communication between your local machine and AWS instances. They provide a secure way to authenticate users without relying on passwords, which are often susceptible to brute-force attacks. However, improper management of SSH keys can lead to unauthorized access, data breaches, and operational disruptions. That’s why it’s crucial to adopt AWS SSH key management best practices to mitigate risks and ensure seamless operations. From key rotation to access control, we’ll explore every aspect of SSH key management to help you build a resilient security framework.
As cloud environments grow in complexity, the need for a structured approach to SSH key management becomes even more apparent. AWS offers a range of tools and features to help you manage SSH keys effectively, but leveraging them requires a clear understanding of best practices. In this guide, we’ll walk you through the steps to implement these practices, ensuring your AWS environment remains secure and efficient. Let’s dive into the details and uncover how you can master SSH key management on AWS.
Read also:Discover The Rich History Of Amarillo Texas A Journey Through Time
Table of Contents
- Why Are AWS SSH Keys Important for Cloud Security?
- How to Set Up SSH Keys in AWS: A Step-by-Step Guide
- What Are the Best Practices for AWS SSH Key Management?
- How to Rotate and Revoke SSH Keys in AWS?
- Why Is Access Control Crucial for SSH Keys?
- How to Monitor and Audit SSH Key Usage?
- Common Mistakes to Avoid in SSH Key Management
- Frequently Asked Questions About AWS SSH Key Management
Why Are AWS SSH Keys Important for Cloud Security?
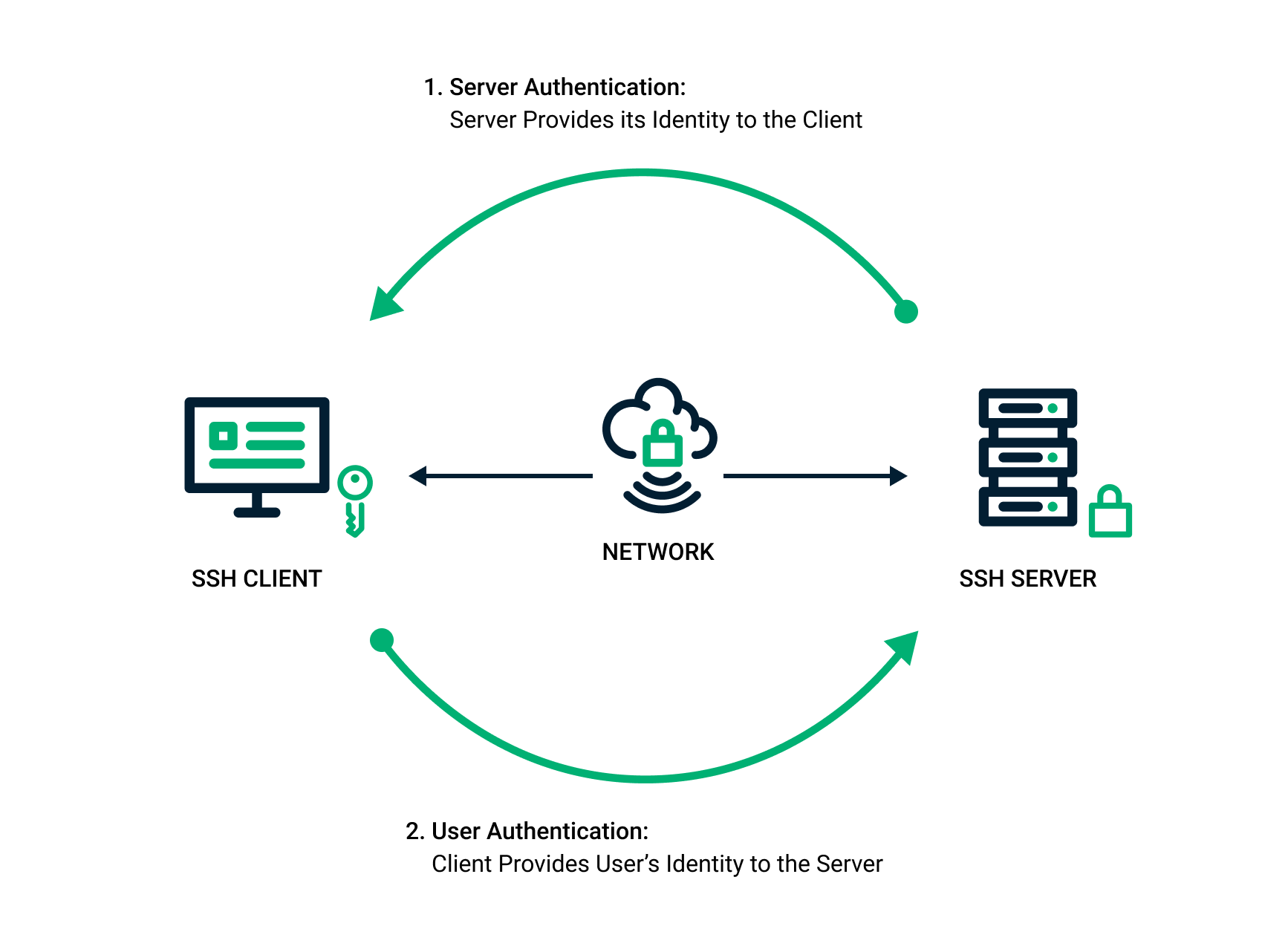
In the realm of cloud computing, security is paramount, and SSH keys play a pivotal role in safeguarding your AWS infrastructure. Unlike traditional password-based authentication, SSH keys use cryptographic techniques to verify the identity of users attempting to access your instances. This not only eliminates the risk of brute-force attacks but also ensures that only authorized individuals can gain entry.
When you deploy an EC2 instance in AWS, SSH keys are used to authenticate users during the initial login. Without a properly configured SSH key, you risk exposing your instance to unauthorized access. Moreover, SSH keys are instrumental in automating processes, enabling seamless integration with CI/CD pipelines, and facilitating secure remote management. By adhering to AWS SSH key management best practices, you can ensure that your keys remain secure and your cloud environment stays protected.
SSH keys also serve as a foundation for implementing the principle of least privilege. By assigning unique keys to specific users or roles, you can control access to sensitive resources and minimize the risk of insider threats. Additionally, SSH keys can be integrated with AWS Identity and Access Management (IAM) policies, providing an additional layer of security. Understanding the importance of SSH keys is the first step toward building a robust security framework for your AWS environment.
How to Set Up SSH Keys in AWS: A Step-by-Step Guide
Setting up SSH keys in AWS is a straightforward process, but it requires attention to detail to ensure security and usability. Below, we outline the steps to generate and configure SSH keys for your AWS environment.
Step 1: Generate Your SSH Key Pair
The first step in setting up SSH keys is to generate a key pair, which consists of a private key and a public key. The private key remains on your local machine, while the public key is uploaded to AWS. To generate the key pair, you can use tools like OpenSSH or PuTTY.
- Open your terminal or command prompt.
- Run the command:
ssh-keygen -t rsa -b 4096. - Specify a location to save the key pair and set a passphrase for added security.
Step 2: Upload Your Public Key to AWS
Once you’ve generated the key pair, the next step is to upload the public key to AWS. This can be done through the AWS Management Console or the AWS CLI.
Read also:How Old Is Lisa Bonet A Comprehensive Look At Her Age Career And Life
- Log in to the AWS Management Console and navigate to the EC2 dashboard.
- Under "Network & Security," select "Key Pairs."
- Click "Import Key Pair" and paste the contents of your public key file.
What Are the Best Practices for AWS SSH Key Management?
Effective AWS SSH key management best practices are essential for maintaining a secure and efficient cloud environment. Below, we discuss some of the most critical practices to follow.
1. Use Unique Keys for Each User
Assigning unique SSH keys to individual users ensures accountability and minimizes the risk of unauthorized access. This practice also simplifies the process of revoking access when necessary.
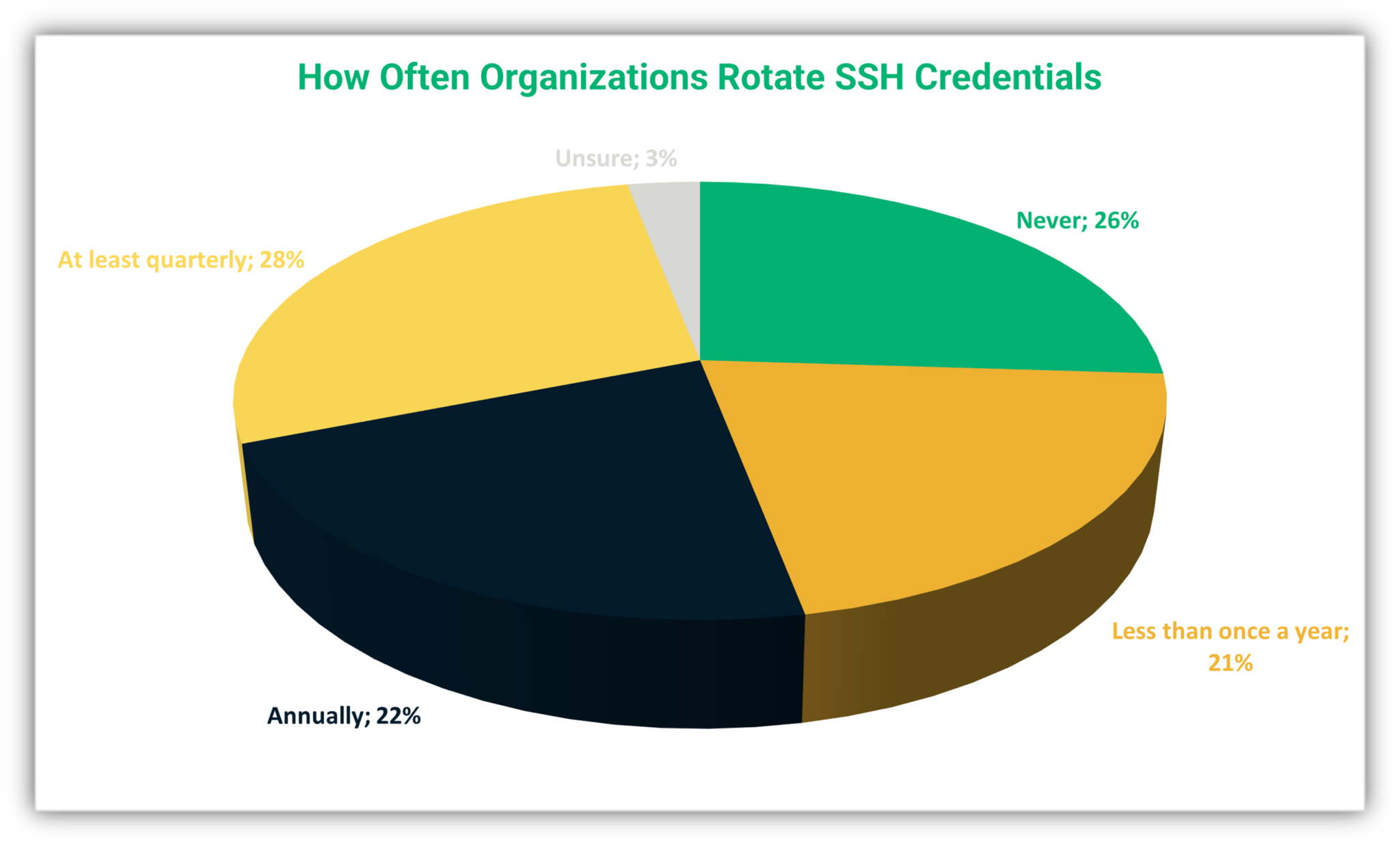
2. Implement Key Rotation Regularly
Regularly rotating SSH keys is a proactive measure to mitigate the risk of compromised keys. Establish a schedule for key rotation and ensure that all stakeholders are informed and aligned.
3. Store Private Keys Securely
Private keys should be stored in secure locations, such as encrypted drives or password managers. Avoid sharing private keys via email or unsecured channels.
How to Rotate and Revoke SSH Keys in AWS?
Key rotation and revocation are critical components of AWS SSH key management best practices. Here’s how you can implement these processes effectively.
Key Rotation Process
Key rotation involves generating new SSH key pairs and replacing the old ones. This process should be performed periodically to ensure ongoing security.
- Generate a new SSH key pair.
- Upload the new public key to AWS.
- Update all instances to use the new key pair.
Key Revocation Process
Revoking SSH keys is necessary when a user leaves the organization or when a key is suspected of being compromised. To revoke a key, simply delete it from the AWS Management Console or CLI.
Why Is Access Control Crucial for SSH Keys?
Access control ensures that only authorized users can access your AWS instances via SSH keys. By implementing role-based access control (RBAC) and integrating SSH keys with IAM policies, you can enforce granular permissions and minimize risks.
How to Monitor and Audit SSH Key Usage?
Monitoring and auditing SSH key usage are vital for detecting anomalies and ensuring compliance. AWS CloudTrail and Amazon CloudWatch can be used to track SSH key activities and generate detailed logs for analysis.
Common Mistakes to Avoid in SSH Key Management
Even experienced professionals can make mistakes when managing SSH keys. Below are some common pitfalls to avoid:
- Using weak or default passphrases for private keys.
- Sharing private keys across multiple users.
- Failing to rotate keys regularly.
Frequently Asked Questions About AWS SSH Key Management
1. How Do I Generate an SSH Key Pair in AWS?
You can generate an SSH key pair using tools like OpenSSH or PuTTY. Once generated, upload the public key to AWS via the Management Console or CLI.
2. Can I Use the Same SSH Key for Multiple Instances?
While it’s technically possible, it’s not recommended. Using unique keys for each instance enhances security and simplifies access control.
3. What Should I Do If My SSH Key Is Compromised?
Immediately revoke the compromised key, generate a new key pair, and update all affected instances. Notify your security team to investigate further.
In conclusion, mastering AWS SSH key management best practices is essential for securing your cloud infrastructure. By following the guidelines outlined in this article, you can ensure that your SSH keys remain secure and your AWS environment operates smoothly. For more information, refer to the official AWS documentation.