In today's world of interconnected devices, remote IoT (Internet of Things) management has become an essential skill for engineers, developers, and IT professionals. If you're looking to connect securely to your remote IoT device using SSH (Secure Shell), this tutorial will guide you step by step through the process.
As the demand for IoT grows, so does the need for secure communication between devices and networks. This article is specifically designed to help you understand how to use SSH for remote IoT device management, ensuring your data remains safe and your operations run smoothly.
Whether you're setting up a home automation system or managing industrial IoT devices, mastering SSH is a critical step. By the end of this tutorial, you'll have the confidence to establish secure connections and manage your IoT devices remotely.
Read also:Unveiling The Power Of 49 Com A Comprehensive Guide To Its Potential
Table of Contents
- Introduction to RemoteIoT Device SSH
- What is SSH?
- Why Use SSH for IoT Devices?
- Biography of Key Contributors to SSH Technology
- Setting Up SSH on Your RemoteIoT Device
- Connecting to Your RemoteIoT Device via SSH
- Enhancing SSH Security for IoT Devices
- Troubleshooting Common SSH Issues
- Best Practices for RemoteIoT SSH Management
- Conclusion and Call to Action
Introduction to RemoteIoT Device SSH
RemoteIoT devices are becoming increasingly common across industries, from healthcare to manufacturing. Managing these devices remotely requires secure communication protocols, and SSH stands out as one of the most reliable options. In this section, we'll explore the basics of SSH and its role in IoT device management.
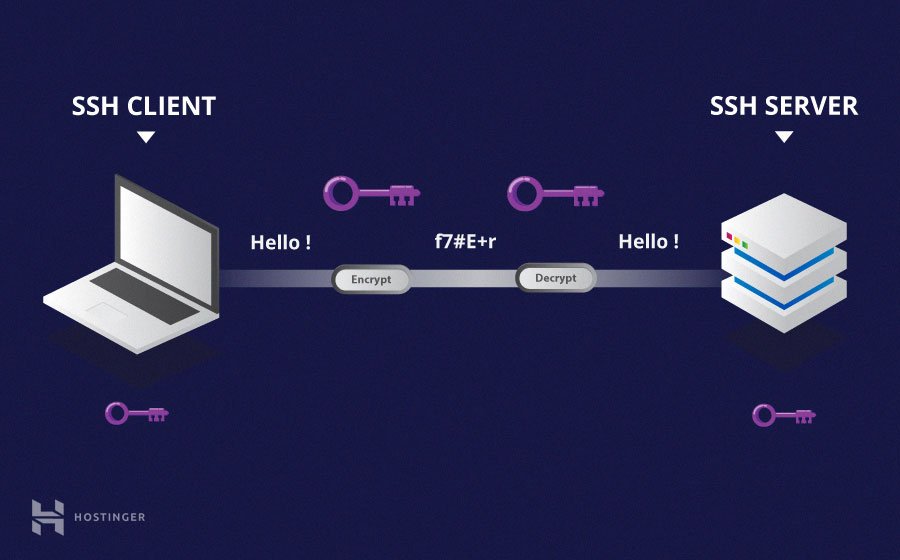
SSH (Secure Shell) is a cryptographic network protocol that facilitates secure communication over unsecured networks. It provides a secure way to access remote servers and devices, making it ideal for IoT applications. By encrypting all data transmitted between your local machine and the remote IoT device, SSH ensures confidentiality and integrity.
For those unfamiliar with SSH, think of it as a digital lock that protects your data from unauthorized access. Whether you're managing a single device or an entire fleet of IoT devices, SSH is an indispensable tool for maintaining security and efficiency.
What is SSH?
SSH, or Secure Shell, is a protocol that enables secure communication between two networked devices. It uses encryption to protect data in transit, making it nearly impossible for attackers to intercept or modify the information being exchanged. Below are some key features of SSH:
- Encryption of data for secure transmission
- Authentication mechanisms to verify user identity
- Support for various cryptographic algorithms
- Ability to execute commands remotely on a server or device
SSH operates on port 22 by default, although this can be customized for added security. Its primary function is to provide a secure channel for remote access, making it perfect for managing IoT devices in environments where security is paramount.
Variations of SSH Protocols
Over the years, SSH has evolved to include multiple versions and extensions. Here are some common variations:
Read also:Festus Haggen The Visionary Leader Revolutionizing Modern Industries
- SSH-1: The original version, now considered outdated and less secure.
- SSH-2: The current standard, offering improved security features and better performance.
- SSH-Tunneling: A technique used to create secure tunnels for transferring data between devices.
Why Use SSH for IoT Devices?
When managing remote IoT devices, security should always be a top priority. SSH offers several advantages that make it the preferred choice for IoT applications:
- End-to-end encryption ensures data privacy.
- Strong authentication methods prevent unauthorized access.
- Compatibility with a wide range of devices and operating systems.
- Support for automation and scripting for streamlined management.
In addition to these benefits, SSH is widely supported by most modern IoT platforms, making it easy to implement and integrate into existing systems. Whether you're configuring sensors, monitoring devices, or updating firmware, SSH provides the tools you need to do so securely.
Biography of Key Contributors to SSH Technology
The development of SSH would not have been possible without the contributions of visionary engineers and researchers. Below is a brief overview of some of the key figures who helped shape this technology:
| Name | Contribution | Year |
|---|---|---|
| Tatu Ylönen | Creator of the original SSH protocol | 1995 |
| OpenSSH Team | Developers of the open-source SSH implementation | 1999 |
| Bruce Schneier | Contributor to cryptographic algorithms used in SSH | 1990s |
Tatu Ylönen, a Finnish computer scientist, developed the first version of SSH in response to a password-sniffing attack on his university network. His work laid the foundation for modern secure communication protocols, revolutionizing how we interact with remote systems.
Setting Up SSH on Your RemoteIoT Device
Before you can connect to your remote IoT device using SSH, you'll need to ensure that SSH is properly installed and configured. Follow these steps to set up SSH on your device:
- Install an SSH server on your IoT device (e.g., OpenSSH).
- Configure the server to listen on the desired port (default is 22).
- Set up user authentication (password or public key).
- Test the connection to ensure everything is working correctly.
For devices running Linux-based operating systems, SSH is often pre-installed. However, you may still need to enable and configure it according to your specific requirements.
Configuring SSH for IoT Devices
IoT devices often have limited resources, so it's important to optimize SSH settings for performance. Consider the following tips:
- Use lightweight cryptographic algorithms to reduce overhead.
- Limit the number of concurrent connections to conserve resources.
- Disable unused features to minimize attack surfaces.
Connecting to Your RemoteIoT Device via SSH
Once SSH is set up on your remote IoT device, you can connect to it using a variety of tools and methods. Below are some common approaches:
- Using the command line: Open a terminal and enter
ssh username@device_ip. - Using an SSH client: Programs like PuTTY (Windows) or Termius (cross-platform) provide graphical interfaces for easier management.
- Using automation scripts: Write scripts to automate repetitive tasks, such as configuration updates or data retrieval.
Regardless of the method you choose, always ensure that your connection is secure and authenticated. Avoid using weak passwords or leaving default credentials unchanged.
Common SSH Commands for IoT Devices
Here are some essential SSH commands you'll likely use when managing IoT devices:
ssh username@device_ip: Establishes a connection to the remote device.scp file_name username@device_ip:/path/to/destination: Transfers files securely between devices.ssh-keygen: Generates public and private keys for secure authentication.
Enhancing SSH Security for IoT Devices
While SSH is inherently secure, there are additional steps you can take to further protect your IoT devices:
- Use public key authentication instead of passwords.
- Disable root login to prevent unauthorized access.
- Change the default SSH port to make it harder for attackers to find.
- Implement firewall rules to restrict access to specific IP addresses.
Regularly updating your SSH software and monitoring for suspicious activity can also help safeguard your devices. Always stay informed about the latest security patches and best practices to maintain a robust defense.
Troubleshooting Common SSH Issues
Even with proper setup, you may encounter issues when using SSH to manage your IoT devices. Below are some common problems and their solutions:
- Connection Refused: Ensure the SSH server is running and listening on the correct port.
- Authentication Failed: Verify your username, password, or public key is correct.
- Timeout Errors: Check your network connection and firewall settings.
If you're unable to resolve an issue, consult the SSH server logs for more detailed information. These logs can provide valuable insights into what might be causing the problem.
Best Practices for RemoteIoT SSH Management
To ensure smooth and secure management of your IoT devices, follow these best practices:
- Regularly back up your device configurations and data.
- Monitor system logs for signs of unauthorized access attempts.
- Limit the number of users with SSH access to your devices.
- Implement role-based access controls to enforce proper permissions.
By adhering to these guidelines, you can maintain a secure and efficient IoT infrastructure while minimizing the risk of security breaches.
Conclusion and Call to Action
In conclusion, mastering SSH for remote IoT device management is a valuable skill for anyone working in the IoT space. By following the steps outlined in this tutorial, you'll be able to establish secure connections, manage your devices effectively, and protect your data from potential threats.
We encourage you to put this knowledge into practice by setting up SSH on your own IoT devices and exploring its capabilities. Don't forget to leave a comment below with your thoughts or questions, and consider sharing this article with others who might find it useful. Together, we can build a safer and more connected world through secure IoT management.