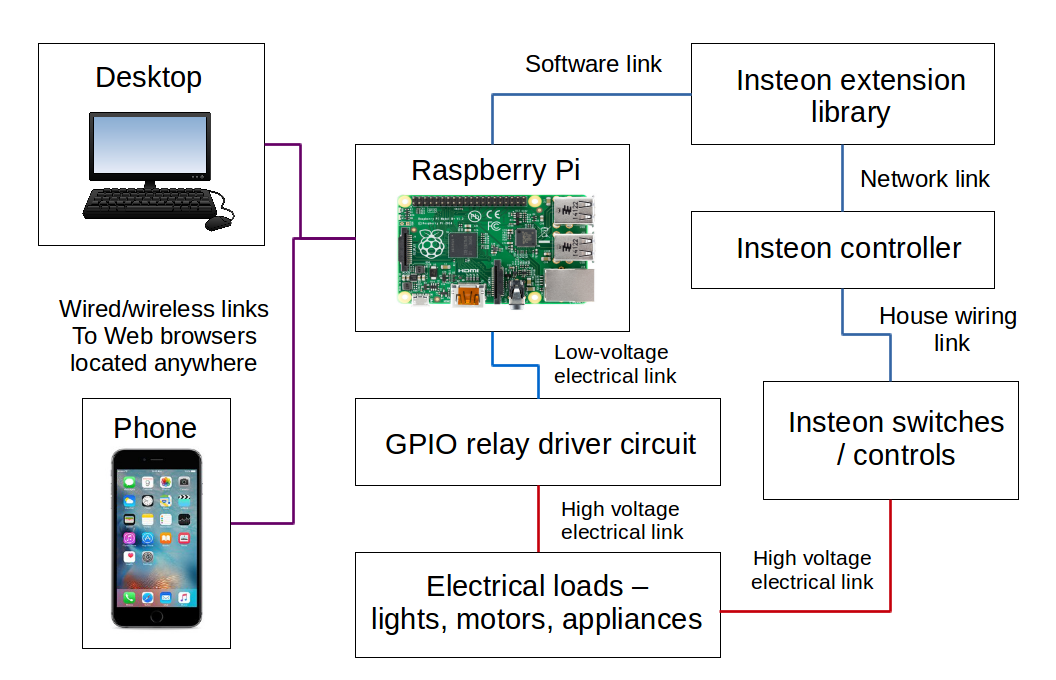
Raspberry Pi secure remote access download has become increasingly popular as more users seek ways to manage their devices remotely. With the rise of remote work and IoT applications, having a secure setup is essential for protecting sensitive data and ensuring smooth operations. Whether you're a tech enthusiast or a professional, this guide will provide you with all the necessary information to set up a secure remote access system on your Raspberry Pi.
In today's fast-paced digital world, remote access to devices is no longer a luxury but a necessity. Whether you're troubleshooting a server, managing IoT devices, or simply accessing files from afar, Raspberry Pi offers a cost-effective and reliable solution. This article will walk you through everything you need to know about setting up secure remote access on your Raspberry Pi.
By the end of this guide, you'll have a clear understanding of how to download the necessary software, configure settings, and ensure your remote access is secure. Let's dive in!
Read also:Harry Enten Married A Deep Dive Into The Life And Career Of The Renowned Political Analyst
Table of Contents
- Introduction to Raspberry Pi Secure Remote Access
- Understanding Raspberry Pi Basics
- Software Requirements for Secure Remote Access
- How to Download Required Software
- Step-by-Step Installation Guide
- Configuring Secure Remote Access
- Implementing Security Measures
- Troubleshooting Common Issues
- Real-World Use Cases for Raspberry Pi Remote Access
- Conclusion and Next Steps
Introduction to Raspberry Pi Secure Remote Access
Raspberry Pi secure remote access download is a critical process that enables users to control their devices from anywhere in the world. This small yet powerful device has revolutionized the way we interact with technology, making it an ideal platform for remote access applications.
Remote access allows you to connect to your Raspberry Pi from another computer or mobile device, enabling you to perform tasks such as file management, system updates, and application monitoring. However, ensuring the security of this connection is paramount to protect your data and privacy.
Understanding Raspberry Pi Basics
Before diving into the specifics of secure remote access, it's essential to understand the basics of Raspberry Pi. This section will cover the fundamental aspects of the device and its capabilities.
Key Features of Raspberry Pi:
- Compact and affordable hardware
- Support for multiple operating systems
- Highly customizable for various applications
- Wide community support and resources
Raspberry Pi is not just a single product but a family of single-board computers designed for hobbyists, educators, and professionals alike. Its versatility makes it an excellent choice for projects ranging from home automation to industrial applications.
Software Requirements for Secure Remote Access
To set up secure remote access on your Raspberry Pi, you'll need specific software that ensures both functionality and security. Below is a list of essential tools and applications:
Read also:Chloe Fineman Scientology The Connection The Truth And What You Need To Know
SSH Client for Secure Connections
SSH (Secure Shell) is a protocol that provides secure communication between two networked devices. It is one of the most commonly used methods for remote access on Raspberry Pi.
- OpenSSH: A widely used SSH client and server software.
- PuTTY: A popular SSH client for Windows users.
These tools allow you to connect to your Raspberry Pi securely and execute commands remotely.
How to Download Required Software
Downloading the necessary software is a straightforward process. Follow these steps to ensure you have everything you need:
Step 1: Download OpenSSH
- For Raspberry Pi OS, OpenSSH is pre-installed. You can enable it via the Raspberry Pi Configuration tool.
Step 2: Download PuTTY (Windows Users)
- Visit the official PuTTY website to download the latest version.
By ensuring you have the correct software, you're setting the foundation for a secure and reliable remote access setup.
Step-by-Step Installation Guide
Now that you have the necessary software, let's proceed with the installation process. This section will guide you through each step to ensure a smooth setup.
Enable SSH on Raspberry Pi
Method 1: Using Raspberry Pi Configuration Tool
- Open the terminal on your Raspberry Pi.
- Type
sudo raspi-configand press Enter. - Select "Interfacing Options" and enable SSH.
Method 2: Using the Command Line
- Open the terminal.
- Type
sudo systemctl enable sshand press Enter. - Type
sudo systemctl start sshto start the SSH service.
Once SSH is enabled, you can connect to your Raspberry Pi from another device.
Configuring Secure Remote Access
Configuring your Raspberry Pi for secure remote access involves setting up the necessary parameters to ensure a safe connection. Below are some key configurations:
SSH Configuration
Edit the SSH configuration file to enhance security:
- Open the terminal and type
sudo nano /etc/ssh/sshd_config. - Make the following changes:
- Set
PermitRootLogin noto disable root login. - Set
PasswordAuthentication noto disable password-based authentication.
sudo systemctl restart ssh.These settings help protect your Raspberry Pi from unauthorized access.
Implementing Security Measures
Security is a top priority when setting up remote access. Here are some additional measures you can take to enhance the security of your Raspberry Pi:
Use a Firewall
A firewall can help block unauthorized access to your Raspberry Pi. Install UFW (Uncomplicated Firewall) and configure it to allow only necessary ports:
- Install UFW by typing
sudo apt install ufw. - Allow SSH access with
sudo ufw allow 22. - Enable the firewall using
sudo ufw enable.
Regularly update your Raspberry Pi's software to ensure you have the latest security patches.
Troubleshooting Common Issues
Even with a well-planned setup, issues can arise. Below are some common problems and their solutions:
Connection Issues
If you're unable to connect to your Raspberry Pi, check the following:
- Ensure SSH is enabled on your Raspberry Pi.
- Verify the IP address of your Raspberry Pi.
- Check your firewall settings to ensure port 22 is open.
By addressing these potential issues, you can ensure a stable and secure remote connection.
Real-World Use Cases for Raspberry Pi Remote Access
Raspberry Pi secure remote access has numerous applications across various industries. Below are some examples:
Home Automation
With Raspberry Pi, you can remotely control smart home devices such as lights, thermostats, and security systems. This not only enhances convenience but also improves energy efficiency.
IoT Device Monitoring
Businesses use Raspberry Pi to monitor IoT devices in real-time, ensuring optimal performance and quick response to potential issues.
These use cases demonstrate the versatility and power of Raspberry Pi in remote access applications.
Conclusion and Next Steps
In conclusion, setting up Raspberry Pi secure remote access download is a valuable skill for anyone looking to manage their devices remotely. By following the steps outlined in this guide, you can ensure a secure and reliable connection to your Raspberry Pi.
We encourage you to share your experience and ask questions in the comments section below. Additionally, explore other articles on our site to deepen your knowledge of Raspberry Pi and its applications.
Thank you for reading, and happy tinkering!